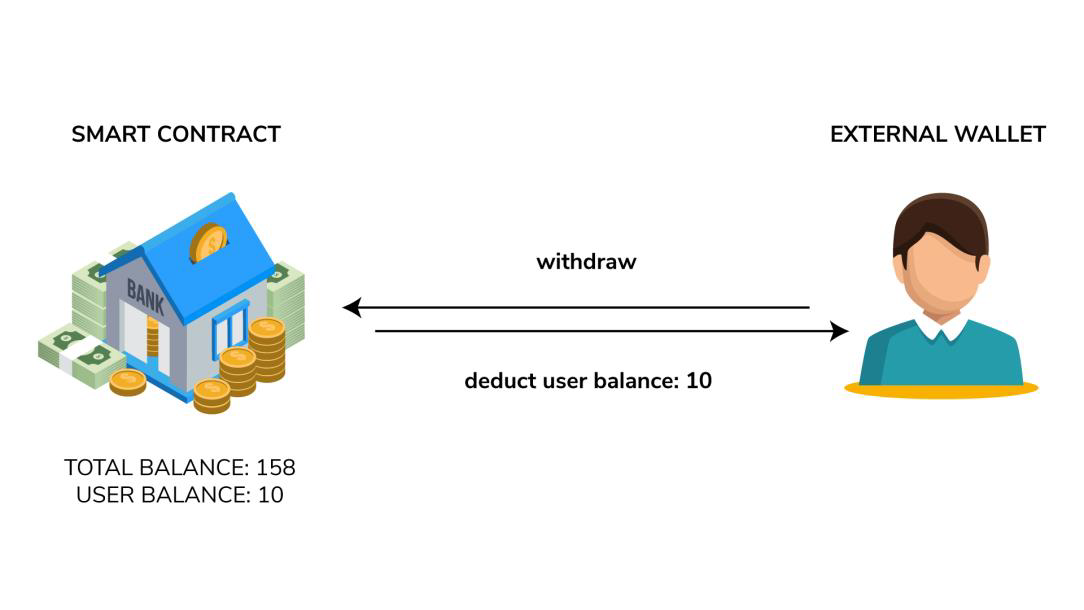
![Smart Contract Attacks [Part 1] - 3 Attacks We Should All Learn From The DAO | by Pete Humiston | HackerNoon.com | Medium Smart Contract Attacks [Part 1] - 3 Attacks We Should All Learn From The DAO | by Pete Humiston | HackerNoon.com | Medium](https://miro.medium.com/v2/resize:fit:988/1*UeDgMZo2n0skHzgkl352zQ.png)
Smart Contract Attacks [Part 1] - 3 Attacks We Should All Learn From The DAO | by Pete Humiston | HackerNoon.com | Medium

How to Avoid Reentrancy Attacks on your Concordium smart contracts — Part 1 | by Concordium | Dec, 2023 | Medium

Smart Contract Attacks: The Most Memorable Blockchain Hacks of All Time - Nextrope - Your Trusted Partner for Blockchain Development and Advisory Services
Future Internet | Free Full-Text | Toward Vulnerability Detection for Ethereum Smart Contracts Using Graph-Matching Network

Reentrancy Attack: Understanding and Mitigating Vulnerabilities in Solidity Smart Contracts | by ismail | CoinsBench

Blockchain smart contracts: Applications, challenges, and future trends | Peer-to-Peer Networking and Applications
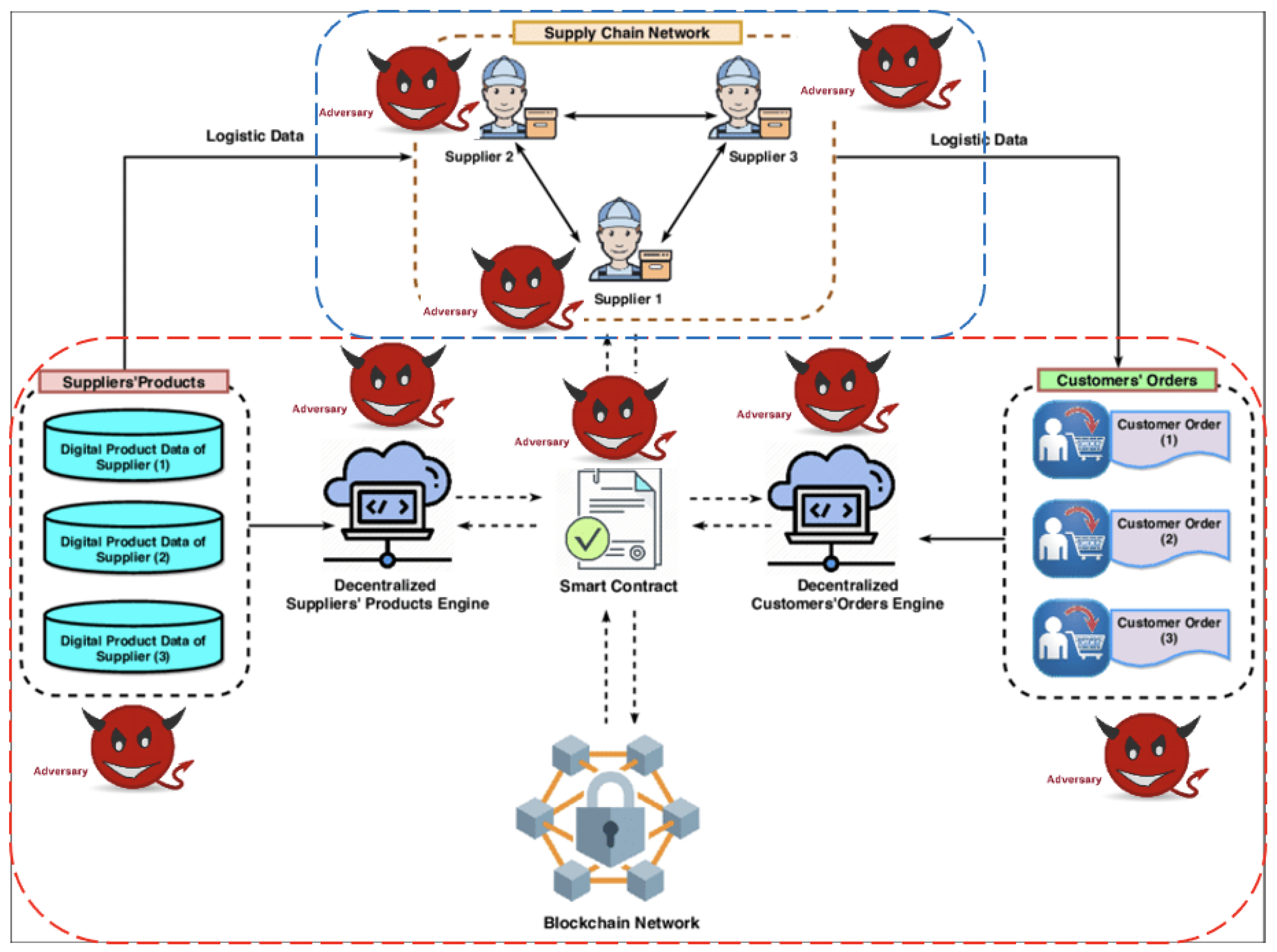

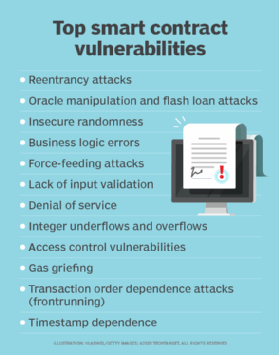


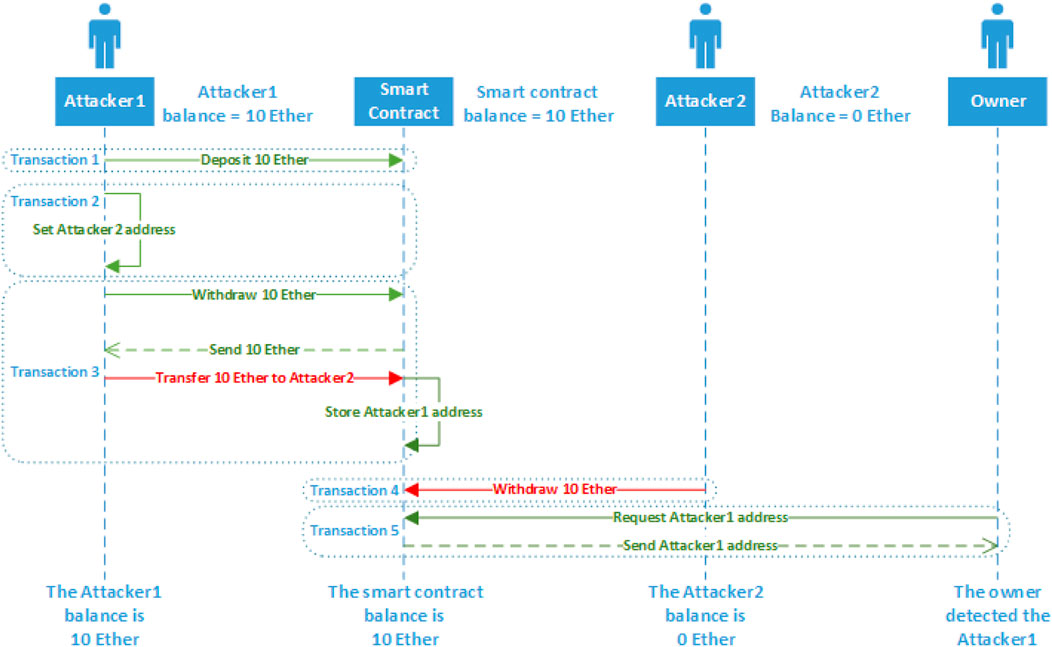



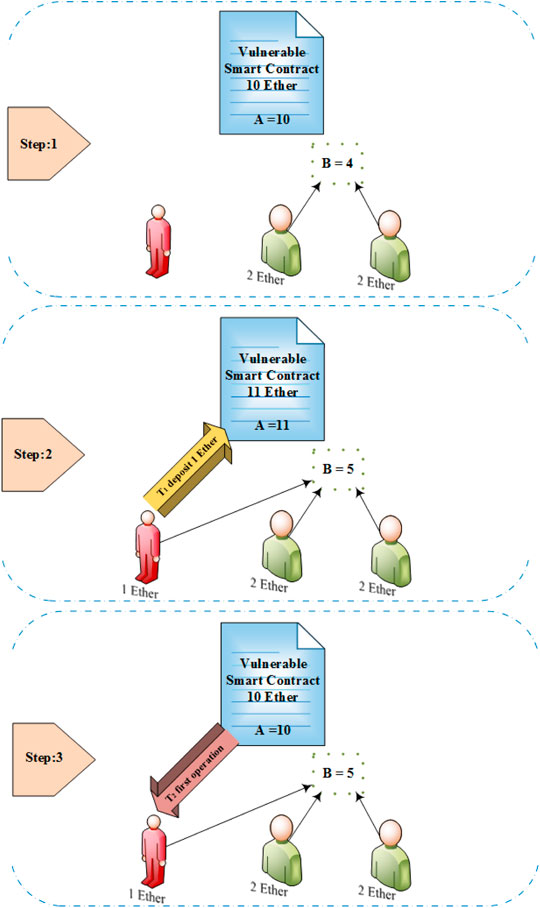
![PDF] Smart Contract: Attacks and Protections | Semantic Scholar PDF] Smart Contract: Attacks and Protections | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/5d30af04fa41ed28d91c621ab51c6f83d9df3296/4-Figure2-1.png)